Self-Signed Certificate
Before you create a self-signed certificate, you should install mod_ssl for Apache httpd server first.
[root@test ~]# yum install mod_ssl
There's a new configuration file /etc/httpd/conf.d/ssl.conf arrived in the installation process.
[root@test ~]# ls -l /etc/httpd/conf.d/
total 36
...
-rw-r--r--. 1 root root 9534 Jul 15 2008 ssl.conf
...
Let's see what we have in ssl.conf.
[root@test ~]# vi /etc/httpd/conf.d/ssl.conf
...
SSLCertificateFile /etc/pki/tls/certs/localhost.crt
...
SSLCertificateKeyFile /etc/pki/tls/private/localhost.key
...
There are two important files that we need to create. And, it seems that we have a very basic certificate on "localhost". Before we test the certification, we should restart httpd first.
[root@test ~]# service httpd restart
Stopping httpd: [ OK ]
Starting httpd: [ OK ]
Let's try to connect to https://localhost/
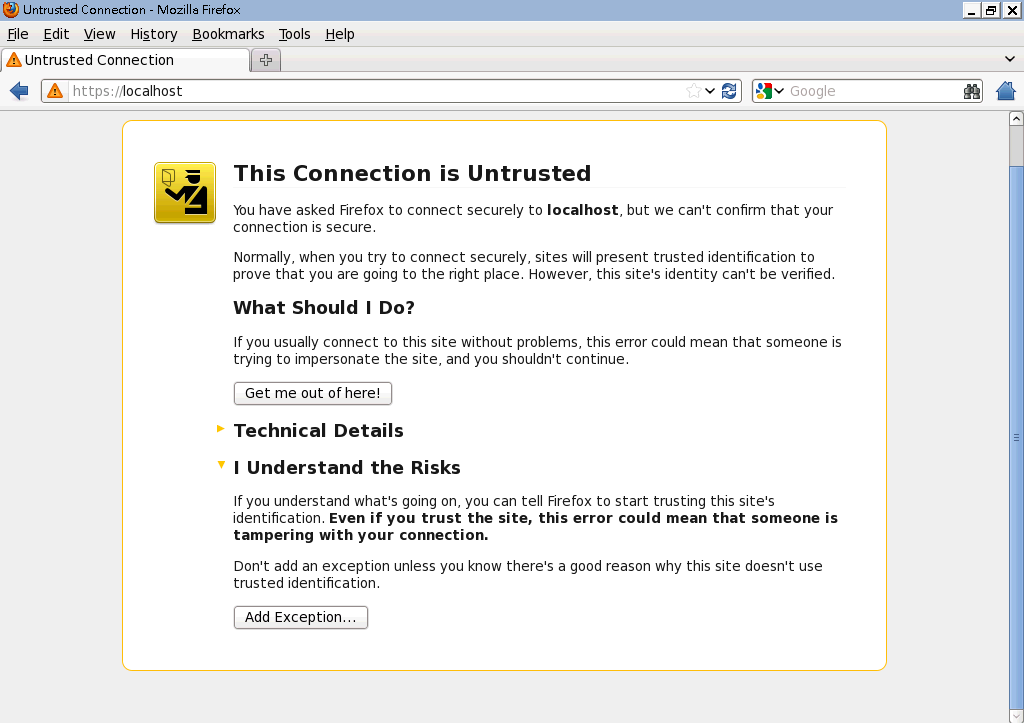
This shows us that the basic certificate on localhost is working as expected, you can just add the site for exception by clicking "Add Exception" button.
Now, back to our topic. Our goal is to create two required files for our domain name (e.g. www.example.com) and then modify /etc/httpd/conf.d/ssl.conf to take them effective.
- A Private Key: /etc/pki/tls/private/www.example.com.key
- A Certificate: /etc/pki/tls/certs/www.example.com.crt
Let's see the steps:
- Create a private KEY.
- Create a CSR:
- Create a CRT:
[root@test ~]# openssl genrsa -aes128 -out /etc/pki/tls/private/www.example.com.key 1024
Generating RSA private key, 1024 bit long modulus
.........++++++
.....++++++
e is 65537 (0x10001)
Enter pass phrase for /etc/pki/tls/private/www.example.com.key:
Verifying - Enter pass phrase for /etc/pki/tls/private/www.example.com.key:
If you do not send the CSR to CA, you can skip the step and use the above private key to create a certificate directly.
[root@test ~]# openssl req -days 3650 -new -key /etc/pki/tls/private/www.example.com.key -out /etc/pki/tls/certs/www.example.com.csr
Enter pass phrase for /etc/pki/tls/private/www.example.com.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:JP
State or Province Name (full name) []:Hiroshima
Locality Name (eg, city) [Default City]:Hiroshima
Organization Name (eg, company) [Default Company Ltd]:example
Organizational Unit Name (eg, section) []:IT
Common Name (eg, your name or your server's hostname) []:www.example.com
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Through a CSR.
[root@test ~]# openssl x509 -req -days 3650 -in /etc/pki/tls/certs/www.example.com.csr -signkey /etc/pki/tls/private/www.example.com.key -out /etc/pki/tls/certs/www.example.com.crt
Signature ok
subject=/C=JP/ST=Hiroshima/L=Hiroshima/O=example/OU=IT/CN=www.example.com/[email protected]
Getting Private key
Enter pass phrase for /etc/pki/tls/private/www.example.com.key:
Or you can create a certificate without taking advantage of CSR by:
[root@test ~]# openssl req -x509 -days 3650 -new -key /etc/pki/tls/private/www.example.com.key -out /etc/pki/tls/certs/www.example.com.crt
Let's check what we have now:
[root@test ~]# ls -l /etc/pki/tls/private/
total 8
-rw-------. 1 root root 887 Mar 20 14:37 localhost.key
-rw-r--r--. 1 root root 986 Mar 20 19:15 www.example.com.key
[root@test ~]# ls -l /etc/pki/tls/certs/
total 1220
-rw-r--r--. 1 root root 571450 Apr 7 2010 ca-bundle.crt
-rw-r--r--. 1 root root 651083 Apr 7 2010 ca-bundle.trust.crt
-rw-------. 1 root root 1147 Mar 20 18:37 localhost.crt
-rwxr-xr-x. 1 root root 610 Jan 9 02:43 make-dummy-cert
-rw-r--r--. 1 root root 2242 Jan 9 02:43 Makefile
-rwxr-xr-x. 1 root root 829 Jan 9 02:43 renew-dummy-cert
-rw-r--r--. 1 root root 936 Mar 20 19:53 www.example.com.crt
-rw-r--r--. 1 root root 692 Mar 20 19:51 www.example.com.csr
Since we already have two required files for SSL, we can modify the configuration file for our domain:
[root@test ~]# vi /etc/httpd/conf.d/ssl.conf
...
SSLCertificateFile /etc/pki/tls/certs/www.example.com.crt
...
SSLCertificateKeyFile /etc/pki/tls/private/www.example.com.key
...
Don't forget to restart httpd. You need to know the pass phrase in advance.
[root@test ~]# service httpd restart
Stopping httpd: [ OK ]
Starting httpd: Apache/2.2.26 mod_ssl/2.2.26 (Pass Phrase Dialog)
Some of your private key files are encrypted for security reasons.
In order to read them you have to provide the pass phrases.
Server www.example.com:443 (RSA)
Enter pass phrase:
OK: Pass Phrase Dialog successful.
[ OK ]
For remote clients, you have to open the port 443 for HTTPS. I recommend you to open the firewall by iptables.
[root@test ~]# iptables -I INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT
[root@test ~]# iptables-save > /etc/sysconfig/iptables
You may also use system-config-firewall-tui like this:
[root@test ~]# system-config-firewall-tui
...
Before you open the port 443, you should backup a copy of current iptables (/etc/sysconfig/iptables) for safety.
Let's test the certificate by connecting to https://www.example.com:
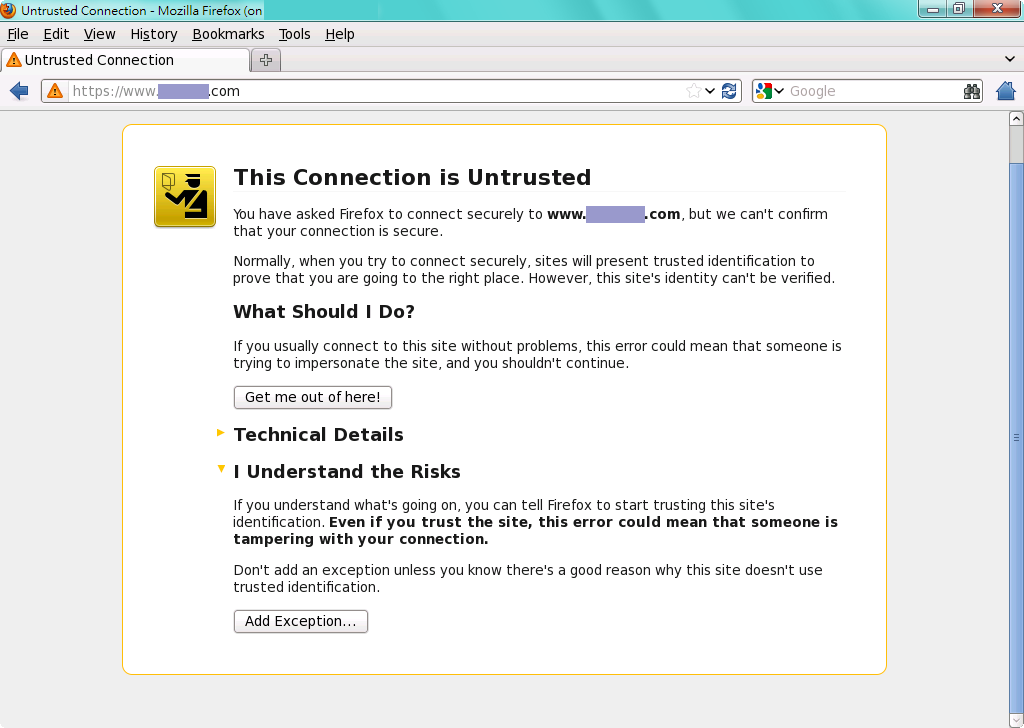
It's done. This is a self-signed certificate. Please tell your users to "Add Exception" on this website. Their communications on this website are all secure now.
For more information, you can refer to this page: Redhat Documentation : 18.1.8. Setting Up an SSL Server.
If you would like to remove the pass phrase of private key, please refer my another post: How to Remove Pass Phrase From Private Key.