XMLRPC Attack
Saw a HTTP attack, it sent 12 to 20 requests per second on /xmlrpc.php, then made web server jam. In HTTP access log, we saw a lot of requests like this:
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
35.185.90.35 - - [03/Mar/2019:21:35:40 -0500] "POST /xmlrpc.php HTTP/1.1" 200 401
Why was the server jammed? That was because we still allowed the public to access /xmlrpc.php, which costed us extra burdens on server to handle the requests. Meanwhile, the database service consumed CPU and IO resources a lot to deal with following queries.
The sources of attacks usually spoof IP addresses that belong to big internet companies. In this case, the attacker spoofed a Google IP to disguise itself as a normal visitor.
Solutions
Several ways that you can secure your server from XMLRPC attacks:
- Deny all requests on /xmlrpc.php
- Rename /xmlrpc.php
1. Deny all requests on xmlrpc.php
You can add a HTTP directive to httpd.conf or .htaccess for denying all requests on /xmlrpc.php.
Suppose the root directory of your virtual host is /wp/virtual-host, we append the directive to .htaccess.
[root@wordpress ~]# vi /wp/virtual-host/.htaccess
...
<files xmlrpc.php>
Order allow,deny
Deny from all
</files>
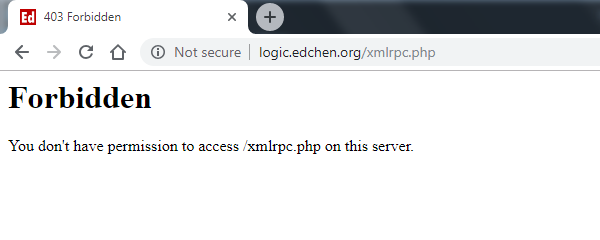
Any attempt will receive a http 403 forbidden header. In HTTP access log, we saw it's different now:
35.185.90.35 - - [03/Mar/2019:21:35:41 -0500] "POST /xmlrpc.php HTTP/1.1" 403 212
Also, unexpected visitors will see the 403 header message like this:
2. Rename xmlrpc.php
In case that you cannot change httpd.conf or .htaccess, you can simply change the filename into a randomized one.
[root@wordpress blog1]# mv xmlrpc.php 4to13j4ig3404-xmlrpc.php
Any attempt will receive a http 404 not found header.
Please note that, HTTP 403 or 404 header consumes very little resources of your WordPress server comparing to HTTP 200 header while attacking. Once the spoofed IP address, the source of attack receive 403, it will stop XMLRPC attack.
Firewall Considerations
Why don't we filter attacks in firewall? Like I said, those IP addresses disguise themselves as normal visitors, you cannot just block IP in firewall as you thought.