The procedure to make a paid Secure Sockets Layer (SSL) work is way more complicate than a self-signed SSL installation, because the procedure involves a third party, i.e. a certificate authority (CA) to take a part, which is responsible to issue a formal certificate for your web server.
In this post, I organized the scattered steps into 10 major steps in sequence to simplify the procedure. In order to make you understand the steps easily, I will explain the steps as little as possible to clarify the concept in the beginnings of this post, after that, I will show the details.
- Make sure required packages installed.
- Create a private key.
- Create a CSR.
- Submit the CSR to your SSL provider.
- Approve the issuance of SSL.
- Get two kinds of certificates.
- Create two files for the two certificates.
- Notify your web server.
- Restart web service.
- Open SSL port on firewall.
In this case, we use openssl to create the private key and Apache httpd as our web server, so we need mod_ssl.
The private key can decrypt the request transmitted from clients by your web server. It also can be used to generate CSR (Certificate Service Request) for CA (e.g. GeoTrust, Comodo).
You don't need CSR, but your CA needs it to create the SSL certificate for your website. In this step, the private key is involved.
There are many SSL resellers in the market, you can get the discounted SSL service through them (e.g. namecheap.com). In order to proceed, you have to submit the body of CSR to your SSL provider.
CA will send you an email that requires your approval on the issuance of the new, formal SSL.
After approval, CA will send you another email containing the newly generated certificates with bodies. The first certificate is your SSL certificate, the second one is the ca-bundle certificate for using in a chain.
You can paste the bodies of the two certificates into your files respectively. Of course, the destination is very important.
So far, your web server has no knowledge about your SSL, so you have to notify the web server by specifying the locations of the private key, SSL certificate, and chain certificate in the configuration file.
It's to make your web server work with the newly configured SSL.
If the firewall is enabled, you should open not only WWW port 80 but also SSL port (i.e. 443) for public to access.
Now, let's see the actual procedure that how I make the formal SSL work.
Make sure openssl and mod_ssl installed.
[root@test ~]# rpm -q openssl mod_ssl
openssl-1.0.1e-16.el6_5.7.x86_64
mod_ssl-2.2.26-2.el6.x86_64
Please update openssl to the newest release to avoid heartbleed. For further information, please refer to my post: How to Update Openssl to a Fixed Release against HeartBleed on Enterprise Linux 6.4
Create a private key.
Please feel free to replace the file name as your needs. In this step, you have to remember the pass phrase of your private key.
[root@test ~]# openssl genrsa -des3 -out /etc/pki/tls/private/www.example.com.key 2048
Generating RSA private key, 2048 bit long modulus
.....+++
.................................................+++
e is 65537 (0x10001)
Enter pass phrase for /etc/pki/tls/private/www.example.com.key:
Verifying - Enter pass phrase for /etc/pki/tls/private/www.example.com.key:
You will need the passphrase every time you start httpd service. To remove it, you can refer to: How to Avoid PassPhrase Dialog.
Create a CSR.
CSR requires your private key as an input, and you have to enter some information for your CSR. In this step, please keep some fields blank as shown as below.
[root@test ~]# openssl req -new -key /etc/pki/tls/private/www.example.com.key -out /etc/pki/tls/certs/www.example.com.csr
Enter pass phrase for /etc/pki/tls/private/www.example.com.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:JP
State or Province Name (full name) []:Hiroshima
Locality Name (eg, city) [Default City]:Hiroshima
Organization Name (eg, company) [Default Company Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:www.example.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
The content of the CSR is like this.
[root@test ~]# cat /etc/pki/tls/certs/www.example.com.csr
-----BEGIN CERTIFICATE REQUEST-----
...
-----END CERTIFICATE REQUEST-----
Submit the CSR to your SSL provider.
I choose namecheap.com as my SSL provider which can let me (1) select the type of web server and (2) fill the body of CSR in an order form. Please be careful, you should include the BEGIN and END lines in the body.
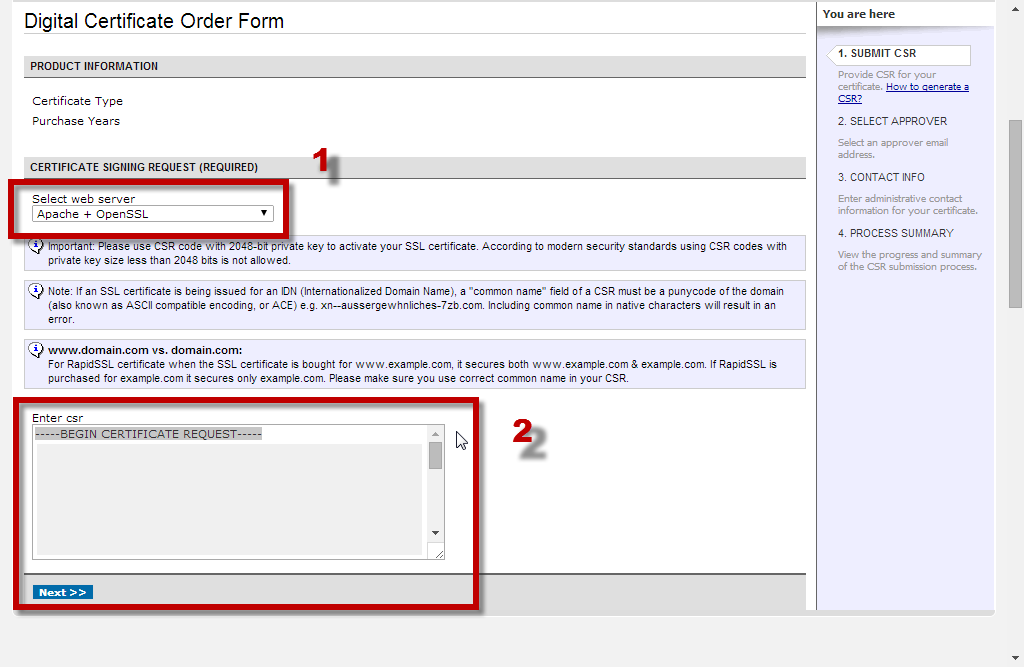
Approve the issuance of SSL.
CA will send you an email that requires your approval on the issuance of the new, formal SSL. Please ask your SSL provider to guide you through.
Get two kinds of certificates.
After approval, CA will send you another email containing the newly generated certificates with bodies. The first certificate is your SSL certificate, the second one is the ca-bundle certificate for using in a chain. Please ask your SSL provider to guide you through.
Create two files for the two certificates.
Once you received the certificate, you have to create two files, one for SSL, and the other is for ca-bundle certificate.
On SSL certificate part, copy and past the body of the SSL certificate into the file, please note that, the file must include the header and footer notation, i.e. BEGIN and END lines:
[root@test ~]# vi /etc/pki/tls/certs/www.example.com.crt
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
On ca-bundle certificate part, upload the ca-bundle certificate to the server.
Notify your web server by editing the configuration file.
You must make sure the following directives are all setup properly.
[root@test ~]# vi /etc/httpd/conf.d/ssl.conf
...
SSLEngine on
SSLCertificateFile /etc/pki/tls/certs/www.example.com.crt
SSLCertificateKeyFile /etc/pki/tls/private/www.example.com.key
SSLCertificateChainFile /etc/pki/tls/certs/ca-bundle.crt
Please make sure the syntax of the configuration file is correct by this:
[root@test ~]# apachectl -t
Syntax OK
Restart web service.
In this step, you must know the pass phrase of the private key to restart httpd service.
[root@test ~]# service httpd restart
Stopping httpd: [ OK ]
Starting httpd: Apache/2.2.26 mod_ssl/2.2.26 (Pass Phrase Dialog)
Some of your private key files are encrypted for security reasons.
In order to read them you have to provide the pass phrases.
Server www.example.com:443 (RSA)
Enter pass phrase:
OK: Pass Phrase Dialog successful.
[ OK ]
Open SSL port on firewall.
You can edit the iptables manually and add the line in the chain:
[root@test ~]# vi /etc/sysconfig/iptables
...
-A INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT
...
Restart iptables to make the new rule effective:
[root@test ~]# service iptables restart
iptables: Setting chains to policy ACCEPT: filter [ OK ]
iptables: Flushing firewall rules: [ OK ]
iptables: Unloading modules: [ OK ]
iptables: Applying firewall rules: [ OK ]
Don't forget to save the result by doing this:
[root@test ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
After the above hard works, you'd better to test SSL from anonymous and remote clients to verify the functionality is fine.